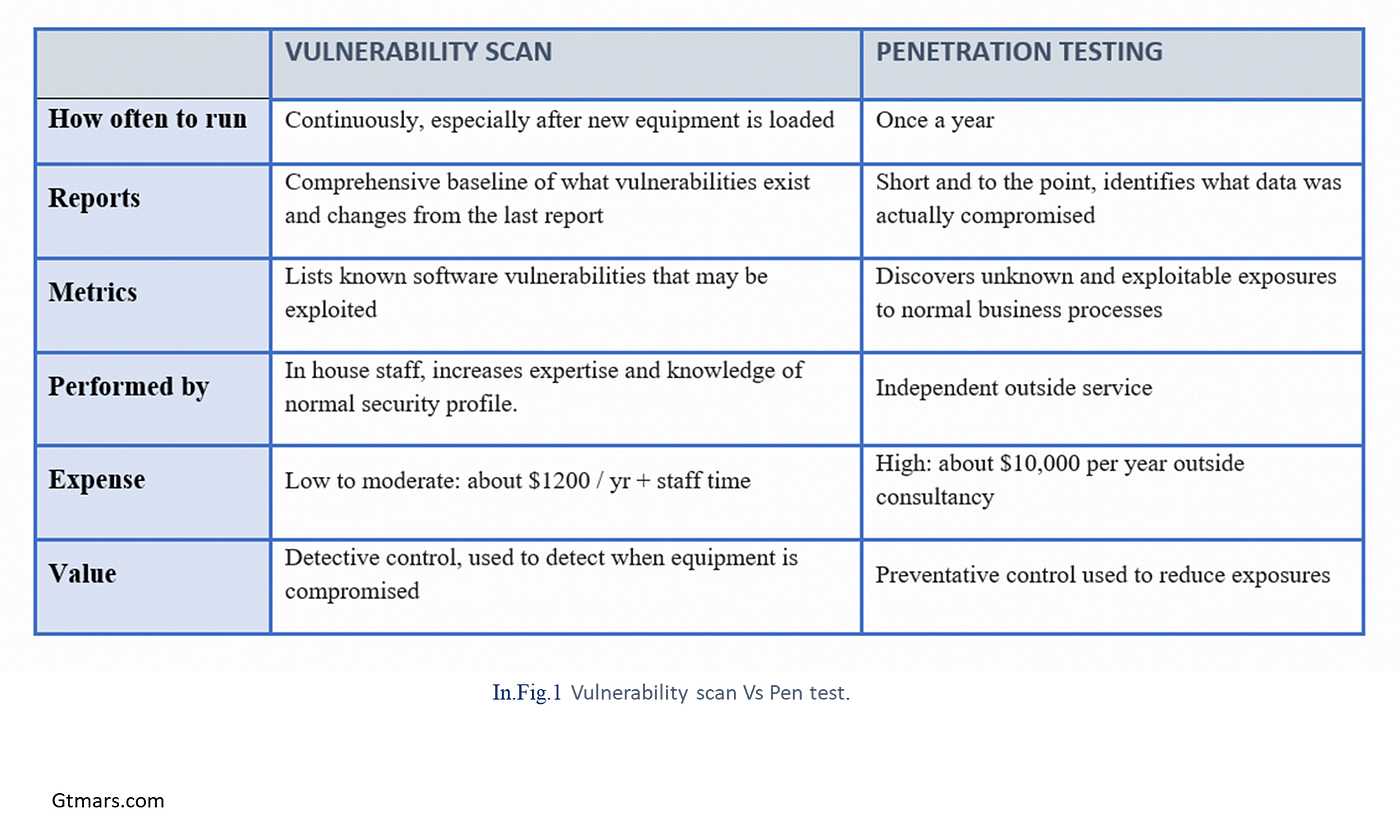
Low-Budget Vulnerability Scanning Guide for Small Businesses: Securing Your Website and Network with Kali Linux and Burp Suite

SafetyDetectives on X: "Do you want to know if there's a threat on your device? We have a FREE VULNERABILITY SCANNER on our site! Scan now: https://t.co/yYqDVYGKuK https://t.co/nWSQkz3994" / X